A version of this article appears on Motherboard
The FBI and DEA aren’t the only law enforcement agencies interested in Hacking Team’s surveillance wares. The Italian company’s hacked emails contain contact information for more than a hundred police departments across the United States, as well as details of in-person demonstrations, including one for the sheriff of Broward County, Florida, which has not previously been reported.
Hacking Team’s rolodex includes domestic law enforcement agencies large and small, from police in such major cities as Los Angeles, Houston and Seattle, to regional fusion centers, to sheriffs in counties you’ve never heard of. There are also district attorneys and even campus cops in the mix.
Most of Hacking Team’s police contacts seem to be culled from law enforcement conferences and compiled for marketing purposes. But a handful of state and municipal police departments have closer ties. Some non-federal agencies have hosted in-person demos, the emails show.
In 2013, for instance, a Hacking Team engineer showed off the firm’s Remote Control System (RCS) for the sheriff’s office in Broward County, near Ft. Lauderdale, Florida, our review of the emails found. This demo has not been reported previously.
According to Hacking Team’s brochure, RCS offers clients “a way to bypass encryption, collect relevant data out of any device, and keep monitoring your targets wherever they are.” The suite exploits security weaknesses in popular websites, including porn hubs, to inject spyware into a target’s device.
The firm is not picky about its customers. Earlier this year, Human Rights Watch called out Hacking Team for selling a remote device monitoring tool to the Ethiopian government. This month’s email dump confirms that the FBI, the DEA, and U.S. military agencies are also Hacking Team clients. But based on a review of the hacked emails, plenty of non-federal agencies are piqued, too.
Whatever your thoughts on the hack, the emails demonstrate interest in advanced surveillance by dozens of police departments nationwide. While MuckRock remains committed to obtaining public records legally, an archive like this tells too much about government dealings to be ignored.
We’ve compiled a map to help mine for domestic agencies that have flirted with Hacking Team. The map below contains all state and municipal domains we’ve found so far in the Hacking Team email dump, as published by WikiLeaks on July 8. For most domains, we’ve also identified the associated agency.
Clicking any agency on the map allows you to search the WikiLeaks archive for all messages sent to or from that agency’s email domain, as well as for messages that contain that domain in the body text.
Note that all links take you directly to the Hacking Team archive on the WikiLeaks website.
The bulk of the state and local police departments named in the emails are on lists pulled from law enforcement conferences. For instance, an October 2014 email lists email addresses for officers of the Kansas Bureau of Investigation, the Houston Police Department, and the Fort Wayne Police Department, among other agencies. The email’s subject indicates that Hacking Team collected contact information during the annual conference of the National Technical Investigators Association (NATIA) in San Diego two months before.
The email archive includes similar contact lists from Law Enforcement Intelligence Units (LEIU) and Intelligence Support Systems (ISS) conferences.
Representatives from Hacking Team gave a number of talks at last year’s ISS conference in Washington, DC, according to the agenda. Notable session titles included “Today’s interception in an encrypted, social and clouded world” and “Intruding communication devices: live demonstration of latest attack techniques.”
In addition to giving conference presentations, the leaked emails indicate that Hacking Team is courting domestic police one-on-one. As has previously been reported, the NYPD and Manhattan District Attorney’s Office arranged a product demo earlier this year, and asked whether Hacking Team software could jailbreak an iPhone remotely.
In 2013, a Hacking Team engineer gave a similar demo for the sheriff’s office in Broward County, near Ft. Lauderdale, Florida.
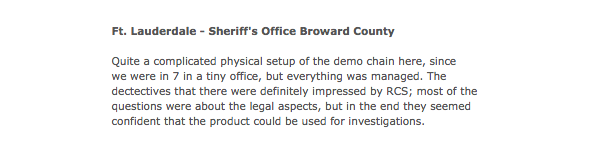
“The detectives that [sic] there were definitely impressed by [Remote Control System],” the engineer summarized in a debriefing email after the demonstration. “[M]ost of the questions were about the legal aspects, but in the end they seemed confident that the product could be used for investigations.”
MuckRock has submitted a request for records concerning the demonstration to the Broward County Sheriff’s Office.
The email indicates that Hacking Team also demonstrated the same system for the Colombian National Police and the United Nations Development Program within days of visiting Broward County.
Hacking Team also reached out to Los Angeles police in 2013 during a US marketing tour.
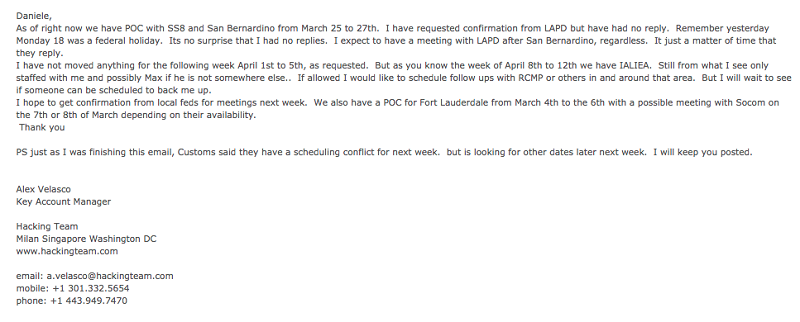
An account manager wrote that it was “just a matter of time that [LAPD] reply,” but the email archives does not indicate whether any meeting took place.
MuckRock will continue to comb the Hacking Team emails using the map above. Help us find U.S. law enforcement agencies with ties to Hacking Team. Send your findings to info@muckrock.com, or by submit a records request of your own by cloning the request we submitted to the Broward County Sheriff.
Use the tag “hacking team” to help us keep track!
Image via Wikimedia Commons




