A version of this article appears on Motherboard
One of the largest sheriff’s departments in the country gushed over Hacking Team, released emails show. After an initial demonstration in 2013, one deputy sheriff in Broward County, Florida told a Hacking Team sales manager, “I can’t see how we can survive without it.”
What follows is easily the most in-depth correspondence uncovered to date between the spyware firm and local law enforcement in the United States.
In July, based on the WikiLeaks archive of leaked Hacking Team emails, we reported that the Italian firm pitched its software to state and local police across the United States. A deeper dive into the emails found that a number of domestic agencies reached out to Hacking Team for in-person product demonstrations. The list of interested agencies includes ones you might expect, like the NYPD and the Manhattan District Attorney’s Office, and others you’d never guess, like the tiny police department at University of California, Santa Barbara.
Newly released emails from the sheriff’s office in Broward County, Florida, provide greater insight into Hacking Team’s courting of non-federal law enforcement in the United States. The Italian firm’s staff made initial contact with a deputy at a conference, offered customized pricing, and provided two on-site demonstrations in quick succession to a “very receptive” command staff.
While Broward County says the sheriff’s office did not ultimately make the purchase, it wasn’t for lack of enthusiasm or effort on the part of Hacking Team salesmen.
A Broward County deputy stopped by the Hacking Team booth at a law enforcement conference in August 2012. Hacking Team makes the rounds at conferences around the world for police investigators and cybersecurity experts, including many such gatherings in the United States. A Hacking Team staffer offered to arrange a demo at the sheriff’s office in Fort Lauderdale.
The Broward County Sheriff’s Office is one of the largest law enforcement agencies in the United States, with more than 5,000 employees and a budget of $730 million. The county sheriff’s jurisdiction covers nearly 2 million people over 1,300 square miles, including a significant portion of the Everglades.
Hacking Team was eager to plug its services.
“I just wanted to see if there was anything we could do for you in this area of investigative tools. Cyber Crime and Cyber Warfare is [sic] not going away, what tools are you taking with you to the fight?” wrote Alex Velasco, a Hacking Team account manager, in a September 2012 email.
The deputy wrote back within a few hours.
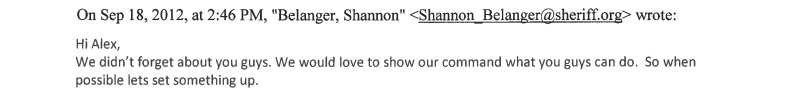
“We would love to show our command what you guys can do. So when possible let’s set something up,” wrote Shannon Belanger, a deputy at Broward County Sheriff’s Office.
Hacking Team made arrangements to come to Fort Lauderdale in January 2013. The sales manager asked for an open port 80 Internet line to demonstrate Hacking Team software, which he noted “is often a problem in government offices.” Deputy Belanger assured that Broward County could accommodate, and asked for a price quote ahead of the demo.
Hacking Team would customize the package and price to suit Broward County’s needs, Velasco wrote back.
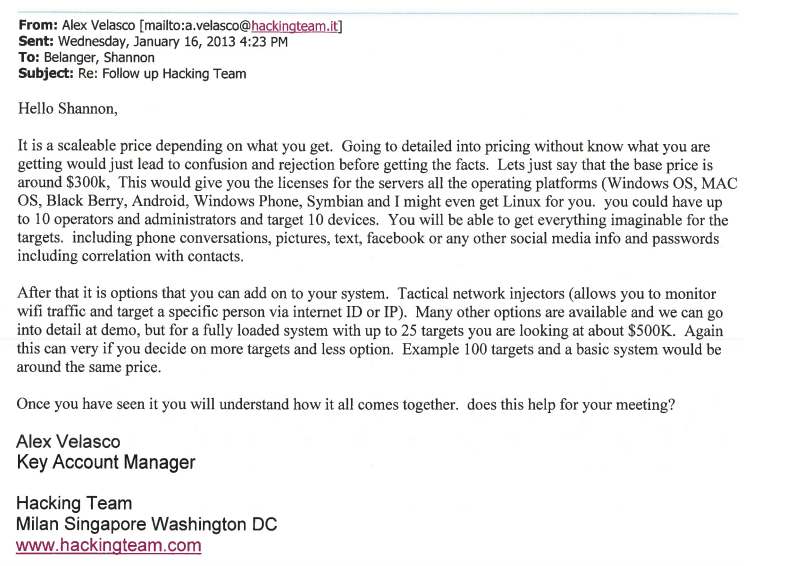
“It is a scaleable price depending on what you get,” the sales manager answered. He explained that approximately $300,000 would get Broward County the base package for Remote Control System (RCS), a spyware suite that exploits security weaknesses in popular websites — including porn hubs — to inject spyware into a target’s device. The latest RCS version in 2013 was called Da Vinci, while the current version is Galileo.
That base package, the email indicates, includes spyware solutions for up to ten operators and ten target devices, with all major mobile operating systems supported. Per the pitch, the sheriff’s office could use Hacking Team’s RCS suite to obtain a broad range of information and communications from target devices.
“You will get everything imaginable for the targets,” Velasco explained to the deputy, “including phone conversations, pictures, text, facebook or any other social media info and passwords.”
The agency could spring for a range of add-ons or expansions from the base package. For $500,000, they could get “a fully loaded system” — presumably with all operating systems and data collection options — for up to 25 targets. Or, for the same price, they could opt for a more basic system for as many as 100 targets.
Hacking Team demonstrated its product in Fort Lauderdale in late January 2013. As we previously reported, the Hacking Team engineer who showed RCS to Broward County thought the demo went well.
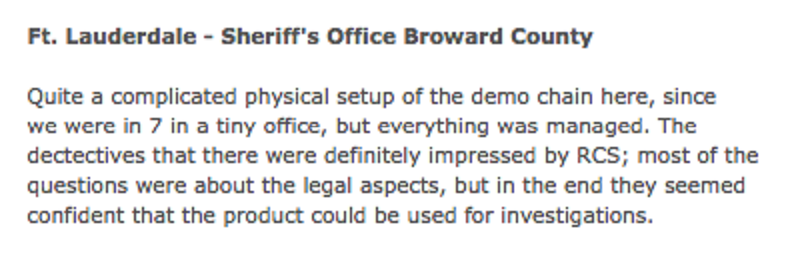
The engineer’s debriefing email described a cramped-but-captive audience of seven in a “tiny office.” The sheriff’s staff liked what they saw, by his read.
“The detectives that [sic] there were definitely impressed by [Remote Control System],” the engineer summarized after the demonstration. “[M]ost of the questions were about the legal aspects, but in the end they seemed confident that the product could be used for investigations.”
During the same demonstration tour, the engineer also showed Hacking Team spyware to the Colombian Navy and National Police in Bogota, as well as the United Nations Development Program (UNDP) in New York City.
The Broward County deputy gushed over the demonstration, as did sheriff’s office command staff, apparently.
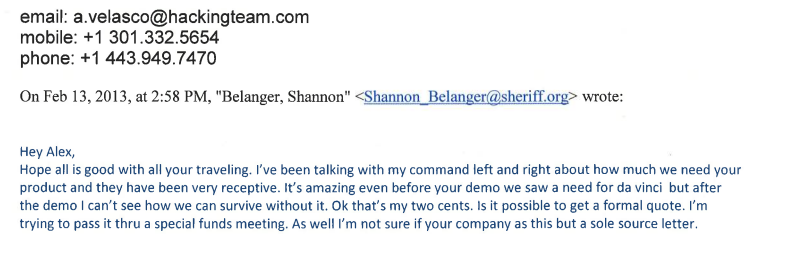
“I’ve been talking with my command left and right about how much we need your product and they have been very receptive,” Deputy Belanger wrote a couple weeks after the initial demonstration.
“It’s amazing even before your demo we saw a need for [RCS] da vinci but after the demo I can’t see how we can survive without it,” the deputy continued.
Belanger asked for a formal quote and other documentation to present at a finance meeting. Hacking Team quickly set up a second “proof of concept” demonstration for early March 2013. The plan was for Hacking Team sales staff to present to several Broward County command staff throughout the day.
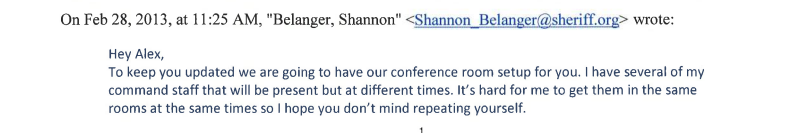
“It’s hard for me to get them in the same rooms at the same times so I hope you don’t mind repeating yourself,” Belanger explained.
Hacking Team did not mind repetition, the sales manager emphasized. Emails released to MuckRock include a confirmation that Hacking Team had arrived in the lobby of the sheriff’s office, as well as a followup a week later thanking Broward County for their time.
Deputy Belanger returned the niceties and asked for an official quote on March 11, 2013. This is where the trail goes cold on Broward County’s interest in Hacking Team. Released emails include advertising newsletters from Hacking Team up to a few months ago for the current version of RCS, but no further correspondence with sales staff.
According to a spokesperson, the sheriff’s office did not purchase Hacking Team software.
“The initial interest was on the part of Belanger who mentioned the product to his command staff and they gave him permission to coordinate a demo,” said BCSO spokesperson Keyla Concepción. “To characterize it as more than that would misrepresent the facts.”
But Broward County Sheriff’s Office did not answer inquiries as to what features of Hacking Team’s spyware caught their interest, or why the agency bailed on the purchase despite initial enthusiasm and two on-site demonstrations.
We’re continuing to dig for police and sheriff’s departments who were in the market for Hacking Team spyware. Broward County is but one of a handful of state and local law enforcement agencies whose correspondence with Hacking Team were in the WikiLeaks dump. It remains unclear whether any non-federal agencies went beyond inquiries and purchased Hacking Team software.
Image via Wikimedia Commons