Task Group Six was an interagency working group for members of the National Security Council on the problem of intelligence compromises. As a result of its study, it made a number of recommendations to improve security and reduce the likelihood of insider threats - changing the way the intelligence agencies did business by putting a natural limit on the scope of their activities. If these policies had been pursued, it’s unlikely that Snowden would have had the justification or the ability to leak the materials he did. Instead, the recommendations that would have seen an actual shift in the status quo were ignored.

Members of Task Group Six came from a cross-section of agencies, including CIA, DIA and NSA to review security breaches and cases of “treasonable activity” in five high profile cases to help prevent security breaches in the future. According to the previously SECRET / NOFORN document, Task Group Six built on the work of “five other integrated damage assessment task groups” which were likely the source of the 21 “additional cases” that Task Group Six reviewed.

The final report of Task Group Six remains classified, as does the work of Task Groups One through Five. The draft document, however, provides insights into Task Group Six’s findings and how the Agency reacted to their recommendations. The findings on the individual cases reviewed by Task Group Six are hardly surprising, and in some cases obvious (at least in hindsight), several of the red flags they raised would later be raised again with notable cases such as Jonathan Pollard’s.
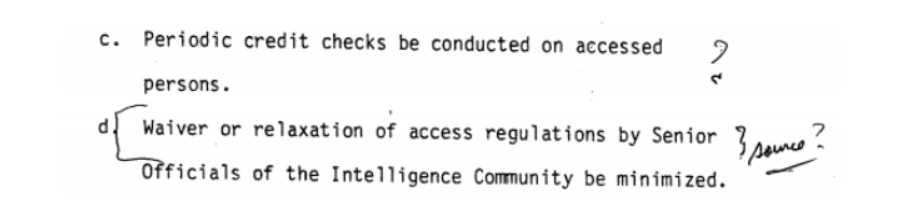
As too often seems to be the case with recommendations relating to counterintelligence, Task Group Six’s recommendations were viewed skeptically by the Agency. Upon recommending that security might be improved if fewer waivers were granted and access restrictions were granted less frequently, the Agency skeptically asked for the source of such an assertion. Similarly, the notion that credit checks could help detect financial anomalies was apparently confusing to the Agency reviewer, despite the report noting that three-fifths of the cases reviewed involved financial considerations.
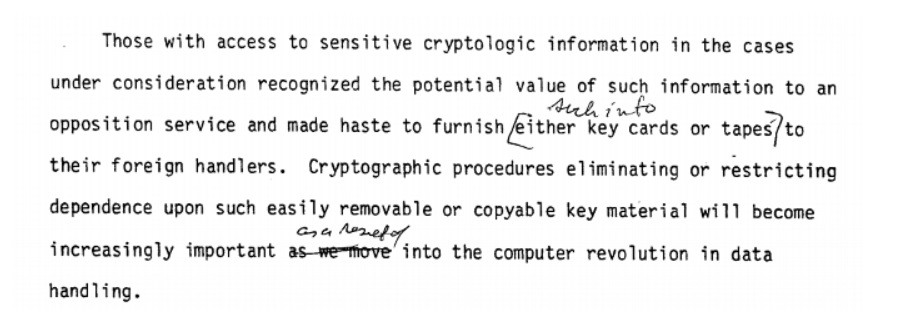
Other recommendations seemed to predict the eventual inevitability of someone like Snowden copying massive amounts of classified information once physical access was no longer required.
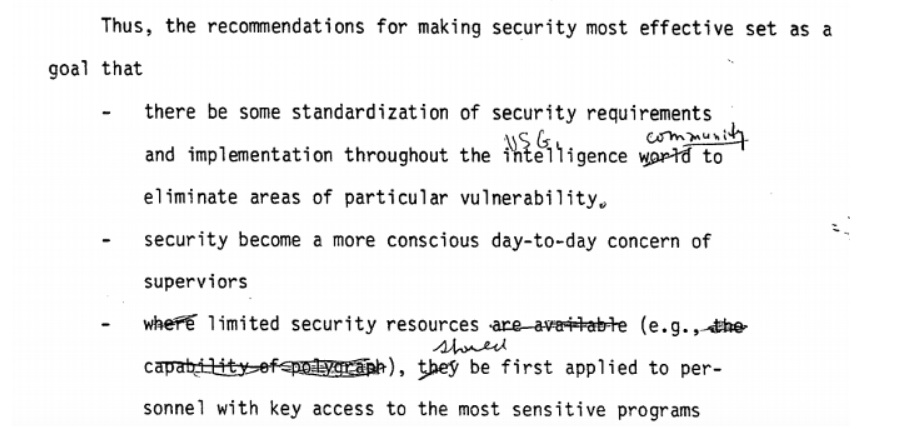
The most revelatory part of the document is the response to Task Group Six’s recommendations in the paper’s summary section. The first three recommendations, which would have seen standardized security requirements implemented, making security more of a “conscious day-to-day concern” and applying limited resources security to the most sensitive programs first, were apparently accepted with little comment. The fourth and fifth recommendations, however, were rejected without comment.
The fourth and fifth recommendations called for limiting the number of personnel on sensitive projects to “security manageable proportions” and extending “principles of enhanced security” to less sensitive programs as resources became available. Both of these recommendations would have greatly aided security procedures, while the former would have also served as a natural limit on the activities (and ultimately on the abuses) of the intelligence agencies. Nevertheless, the Agency reviewer X-ed out these recommendations. No explanation for this is provided, but given the recommendations undeniable efficacy, it’s likely because they would have limited the scope of the Intelligence Community’s activities.
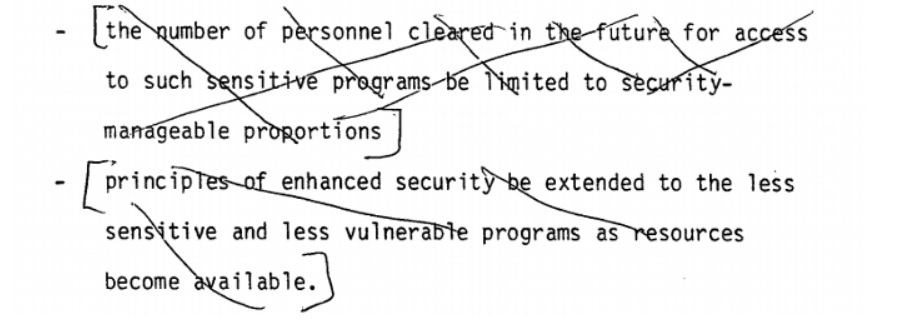
Limiting the number of personnel cleared for these programs to security-manageable proportions would have introduced a natural limit to the scope of intelligence activities, forcing the Agencies to prioritize more and only proceed with operations in the safest way possible - instead of doing things like allowing the date and location of Bay of Pigs invasion to leak to the Soviets, then proceeding with it anyway. It also would have put a serious limit on things like mass surveillance, which would have negated the justification for the Snowden leaks while likely also making them impossible.
Other methods of limiting espionage and leaks, such as “physical measures which might be taken to eliminate illegal document reproduction or removal,” are quickly dismissed as “so onerous they would unacceptably obstruct the carrying out of normal required business” - conveniently absolving the agencies involved. Based on the declassified draft report prepared by Task Group 6, they spent little to no time exploring these issues or other ways of addressing them. Most of the focus was limited to the people who had committed treasonable espionage, hoping for prevention or early detection of insider threats.

Treasonable behavior was, according to Task Group Six and their reviewer, likely to result from “latent immaturity, egocentricity, instability, mid-life crisis and financial consideration.” By focusing on these, the Agencies affected by Task Group Six’s recommendations were able to largely avoid changing their way of doing business. While Task Group Six sought to explore “the role thoughtless management can play in abetting espionage,” the thoughtless management Task Group Six explored focused on inconsistent application of security procedures across agencies, rather than actually altering the management style or the way counterintelligence was approached within the agencies.

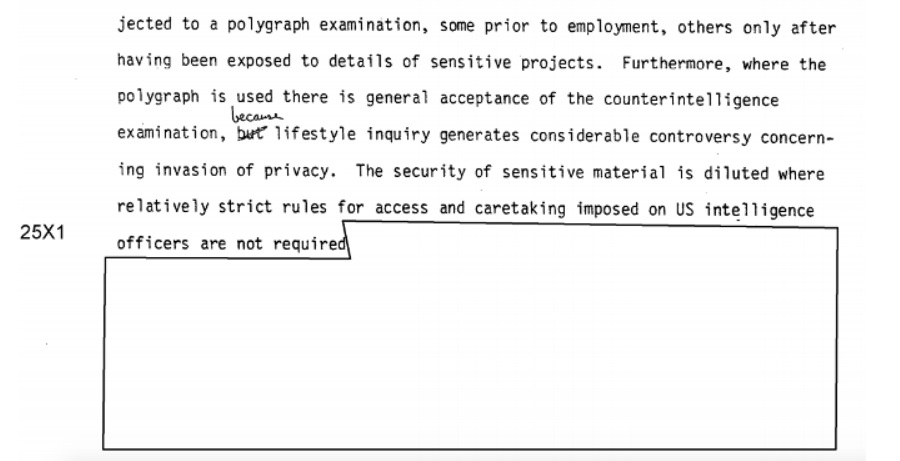
As a result, only the recommendations that consisted of “more funding, do more of what you were doing, and use polygraphs more” were considered. Things that would have changed the way the Intelligence Community approached things, such as limiting projects to security-manageable proportions, were ignored in favor of focusing on the psychological and emotional shortcomings of potential insider threats and increased use of the polygraph, a test known to produce results which are both unreliable and racially biased.
Other recommendations seemed to strongly parallel ones that had long been made by Angleton, such as pooling all available information on employees and providing security and counterintelligence personnel direct access to these files.

The specter of the discarded recommendation of limiting things to security-manageable proportions was re-raised later in the report when Task Group Six pointed out that the accountability systems had been overtaxed, turning secure facilities into “secure” facilities where a “determined thief can easily avoid detection.” Further limiting access to copy machines was eventually instituted, along with document marking systems for both digital copies and physical printouts. Nevertheless, by Task Group Six’s own estimation these addressed only the symptoms of a systemic problem.

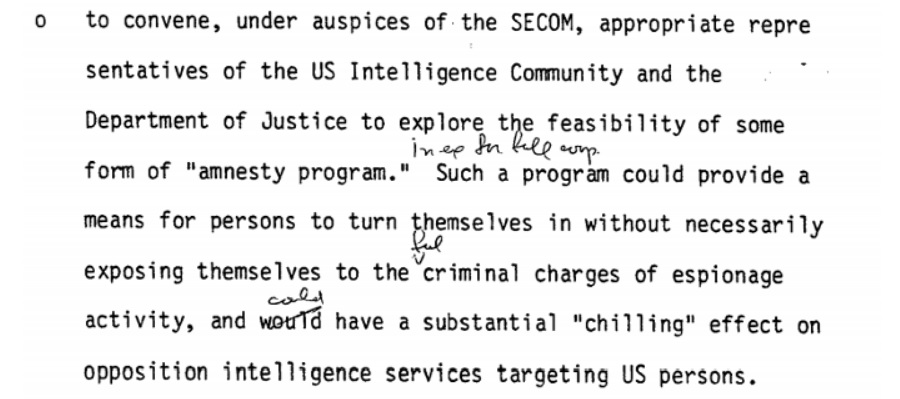
The most useful recommendation from Task Group Six that doesn’t seem to have been discarded out of hand was looking into implementing an amnesty program which might provide an “out” for people who’d been compromised by a Foreign Intelligence Service in a way that might otherwise see them further exploited. By reducing the potential for blackmail, which can all too often be created by the actions of the intelligence agency trying to avoid it, long-term threats could be potentially mitigated.
Had Task Group Six’s full set of recommendations been adopted, then several decades of the Intelligence Community’s history likely would have changed due to more proportionate programs and fewer leaks. Instead, the Agency reviewer nixed nearly every recommendation that didn’t boil down to “the status quo, but more of it.”
You can read the declassified sections of the report below.
Like Emma Best’s work? Support her on Patreon.
Image via Warner Bros.




