Smart FOIA requests recently have shown how a government database has channelled neighbor vs. neighbor feuding, shown which journalists and activists get under an agency’s skin, and helped dig into how Trump officials are spending their time. Plus a new access audit finds generally good news out of Illinois, but that agencies still forget to sweat the small stuff.
If you’re feeling inspired by these requests, file a public records request of your own. And if you find a FOIA story worth sharing, send it over via email, on Twitter, or on Facebook, and maybe we’ll include it in the next roundup.
Looking inside the Victims of Immigration Crime Engagement (VOICE) hotline
Daniel Rivero and Brendan O’Connor have a remarkable story for Splinter looking into the Victims of Immigration Crime Engagement (VOICE) hotline. Based largely on a FOIA request, as well as another improperly redacted database that they found thanks to the FOIA’d database, the reporting shows how a complaint hotline created to showcase crimes committed by “removable aliens” quickly became a hive of neighbors ratting out neighbors, family members trying to use immigration authorities to get step children deported, and spouses retaliating when accused of domestic abuse.
Caller requested to report her mother-in law and sister-in law. Caller stated these individuals came to the U.S. as tourists and stayed in the U.S. in order to get legal status. Caller stated the undocumented individual is destroying her family and is committing adultery. Caller requested to report his ex wife that is undocumented as an overstayed on her visa. Caller requested to report the illegal alien because the illegal alien will not let her see [her] granddaughter.
And while publicly the database was touted as a way to help victims, the reporters found it ended up being more about enforcement:
Publicly, the VOICE hotline is not supposed to be a crime-reporting tool at all, but a means of connecting victims and witnesses in existing cases with support services and with more information about the people accused. But internal training materials for the hotline, obtained by Splinter, contradict that mission statement, saying that the hotline “will provide a means for persons to report suspected criminal activity.” Callers were often referred to the Homeland Security Investigations tipline. In several cases, VOICE employees contacted a field office to relay information gleaned from the calls, records show.
To make matters worse, ICE also had apparently posted an unreacted version of the database online, which Splinter’s reporters found. It included cell phone numbers of complainants, home addresses, and other very personal information, included on domestic abuse victims.
After Splinter’s story, ICE ask that they destroy or return the data used for it in a vaguely worded but somewhat threatening letter. ICE also removed its entire FOIA reading room after the Splinter story went live.
“This was based on a FOIA I threw out on a whim a few months ago that ended up leading to a bigger, better story,” said Rivero in an email. “I think the big lesson here is that FOIAs can be used as just jump-off points, and that sometimes the government screws up and publishes things that are buried so deep on their website that no one sees them–until they do. Go a step beyond just the document, I guess?”
He also shared how the FOIA helped him get the bigger story of improperly released information:
This story came after I FOIAd the call logs, and I noticed that they left a single police report number unredacted, along with a mention of a city that had a prison where the suspect was being held. I searched the police report number and the city on Google just out of curiosity and just WHAM found this bigger spreadsheet with all sorts of superpersonal info that included that particular case. As soon as I saw it I knew that something was very wrong. If one of the suspects were to just Google themselves and their city, say, this downloadable sheet would have been one of the first results. But then there were so many terrifying tidbits in there, we struggled about which story to lead with–the breach or the story about how people were using the new hotline? We decided to kind of merge it into one big story. Now ICE is comically demanding that I return the spreadsheet.
As soon as the VOICE program was announced I knew that there would be gold in there somewhere. Any new, niche program that will clearly create a papertrail has a few elements that I always try to look out for: 1) You know exactly what to ask for. It’s a hotline–ask for call logs! 2) Politically, it is so new that they might be naive in how they were gathering documents. They might not have had the conversation they are probably having right now, which is “how are we handling this information, and should we be commingling all of that info into one column and not isolating it in different columns to make redaction easier?”
New kid on the blocklist
Luke Stoddard Nathan has a piece for The Alt taking a look at the Twitter block list of AIM Photonics, a Rochester-based research consortium which receives hundreds of millions in state funding. The Alt requested the information the day Nathan had discovered he had been blocked by @AIMPhotonics.
The resulting release showed the blocklist was mostly spam bots, but included two humans: Nathan as well as another Twitter user who had made a mild rebuke of the consortium. The block list also included a parody account of the state’s governor.
But the request apparently got more results than just the released documents:
update: @AIMPhotonics has unblocked me. Thank you. pic.twitter.com/u37lEzqHgj
— Luke Stoddard Nathan (@lukestdnathan) August 30, 2017
Like Schroedinger’s Cat, sometimes just filing a request can change the requested documents.
Here’s another example of a request for a Twitter block list that was successful in Kentucky which you can clone and tweak to file if you’d like to dig into similar issues. You can even request direct messages from agency accounts.
The piece also reminds me about a story we did several years ago digging into a secretive private account the Department of Homeland Security ran.
EPA chief Scott Pruitt’s calendar
The New York Times has a well-researched and documented dive into a day-in-the-life of Environmental Protection Agency head Scott Pruitt:
For lunch on April 26, Scott Pruitt, the new administrator of the Environmental Protection Agency, dined with top executives from Southern Company, one of the nation’s largest coal-burning electric utilities, at Equinox, a white-tablecloth favorite of Washington power brokers.
That evening, it was on to BLT Prime, a steakhouse inside the Trump International Hotel in Washington, for a meal with the board of directors of Alliance Resource Partners, a coal-mining giant whose chief executive donated nearly $2 million to help elect President Trump.
Before those two agenda items, Mr. Pruitt met privately with top executives and lobbyists from General Motors to talk about their request to block an Obama administration move to curb emissions that contribute to climate change.
It was just a typical day for Mr. Pruitt, the former Oklahoma attorney general.
They were able to get that level of detail thanks to a FOIA request that netted over 300 pages of Pruitt’s daily calendar. One interesting thing that the Times notes: It wasn’t actually their request that netted the documents, but American Oversight. The Times had actually requested the same information, but the EPA had not provided the documents. The difference: American Oversight sued.
Illinois audit finds mixed results
DR. A. Jay Wagner and Sophie Honeyman of Bradley University have an audit Illinois Freedom of Information Act up.
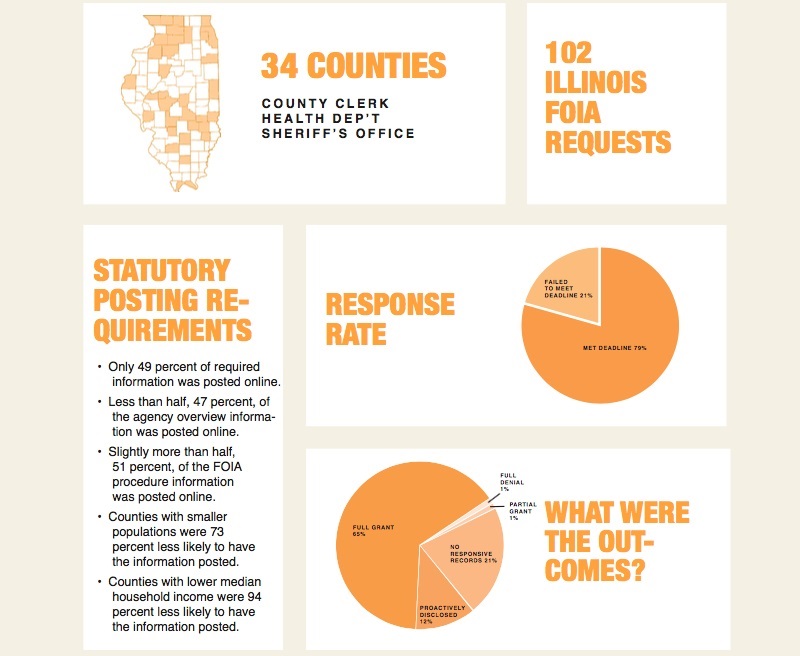
The audit followed the fairly standard formula of filing a routine request and checking compliance, and generally gave good marks. Less standard was that the audit looked for material proactively provided, and found that many agencies weren’t following through on their commitments. The audit specifically looked at which agencies proactively posted contact information for public records officers, and round that only roughly half did.
“While the sampled counties scored admirably in delivering the requested information - frequently by the deadline and generally with little trouble - the counties performed poorly in the more mundane elements of FOIA compliance,” the study found. “They collectively struggled to provide the necessary information to file a FOIA request.”
I try to keep a running tab of audits, so if you know of one please let me know via email or check out the list I’ve compiled. And if you’re interested in running an audit of your own, get in touch with us: We’d love to collaborate.
In the meantime, if you see a great use of FOIA or have one of your examples you’d like to share, send it over via email, on Twitter, or on Facebook, and maybe we’ll include your story in the next roundup.
Image by Fibonacci Blue via Wikimedia Commons and licensed under Creative Commons BY-SA 2.0.




