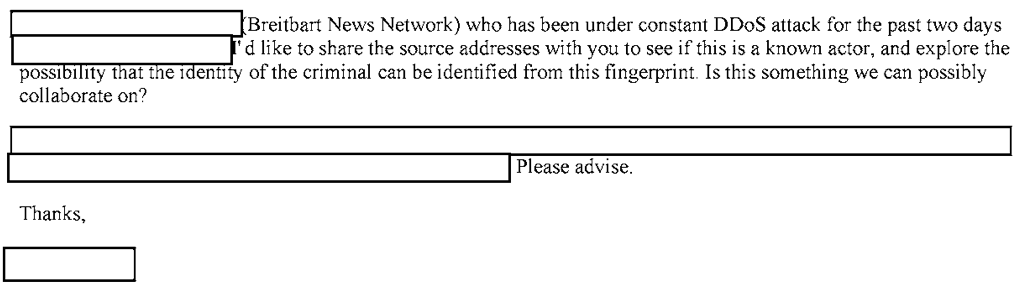
On January 17, 2016, the alt-right news site Breitbart found itself under siege: A number of IP addresses were sending a large amount of traffic its way, straining its servers. Writing to the FBI two days later with the subject line “Request for assistance,” someone (identity redacted) shared the source of the IP addresses and asked that the FBI “explore the possibility that the identity of the criminal … be identified from this fingerprint.”
Things kept getting worse …
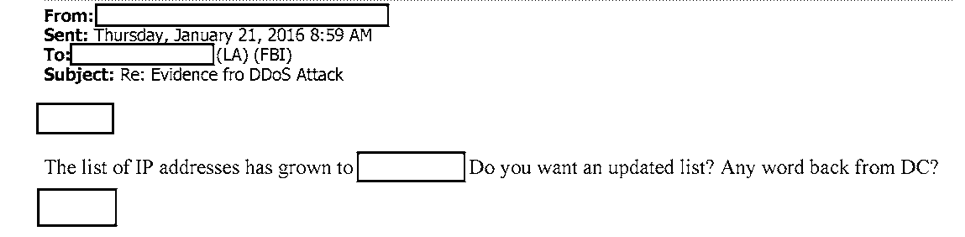
and the Bureau took some time to investigate the issue.
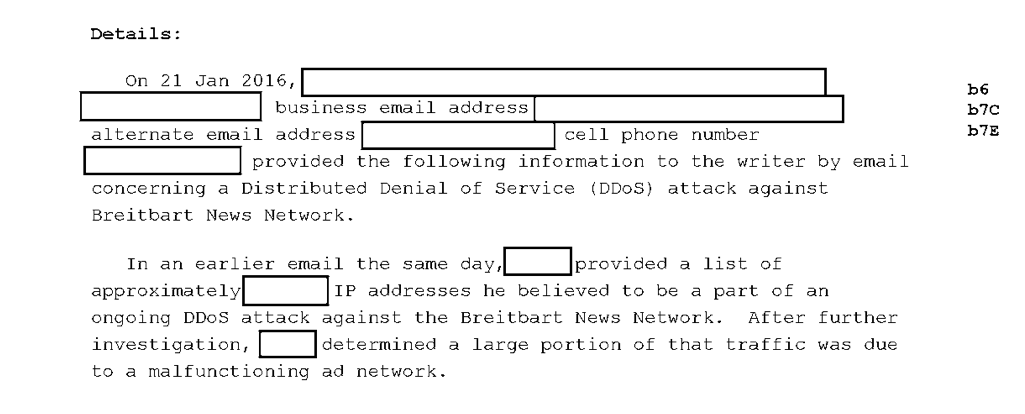
Eventually, the technical contact at Breitbart resent the list of IP addresses sending traffic but, this time, excluded ad network traffic. Turns out, there wasn’t much of a problem after that.
These things happen. While we don’t run ads on MuckRock (instead relying on the generous support of readers like you), poorly configured scrapers have taken down our site before and when everything is going to hell, it’s easy to jump to conclusions.
You can’t say that they didn’t have any warning that this sort of thing could happen though:
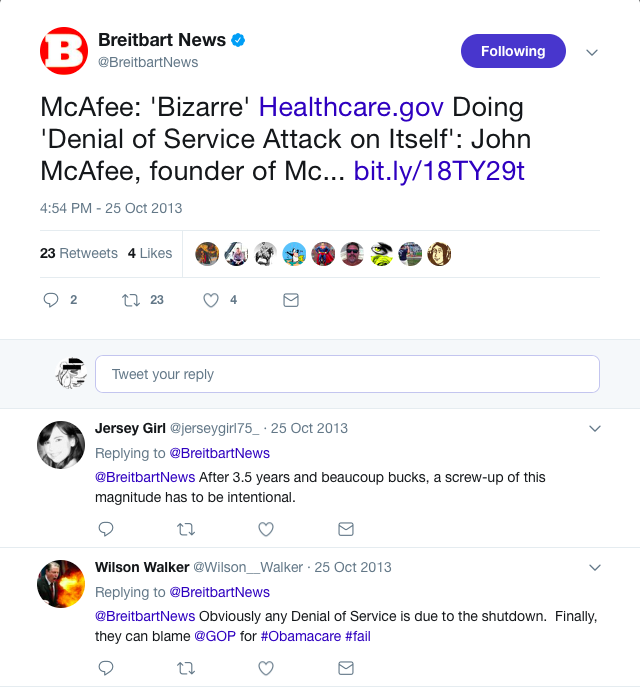
But maybe more interesting than the inadvertent self-own is what the FBI didn’t releases: 1,460 pages that were fully redacted, according to the agency.
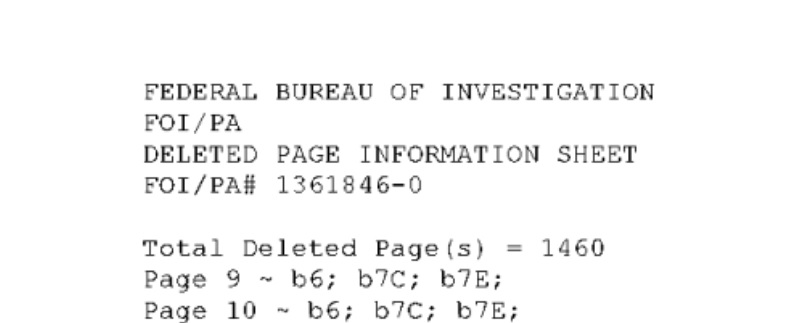
Almost all of them were redacted from release under exemptions b(6), b(7)(c), and b(7)(e). But what do they withhold?
Tough to tell, but it seems that even that accounting of withholdings may not be complete, because Jason Leopold got a letter that indicated even more documents were being withheld, pending a current law enforcement proceeding, under b(7)(A).
There is an ongoing law enforcement investigation that involves Breitbart News as indicated by this response to my @_rshapiro #FOIA pic.twitter.com/rsIAHg34tl
— Jason Leopold (@JasonLeopold) September 13, 2017
Guess we’ll have to keep filing new requests until that proceeding is completed to find out. In the meantime, also check out FCC complaints mentioning Breitbart, or read the full FBI files on Breitbart embedded below, or on the request page.
Image by Michael Vadon via Wikimedia Commons and licensed under Creative Commons BY-SA 4.0.